This post is a followup from my post 802.11 State Machine. The 4-way handshake is a process between the Client (Supplicant) and the AP (Authenticator) were EAPOL-Key frames are exchanged with the goal to secure communications between them. Both WPA2-Private(PSK) and WPA2-Enterprise (802.1X) use this process to form a Robust Security Network Association (RSNA).
The goal with the process is to derive keys to encrypt information.
First frame is send by the Authenticator and contains a ANonce used to generate the Pairwise Transient Key(PTK). The frame also contains information about what encryption is being used.

The Supplicant now has enough information to resolve a Pairwise Transient Key(PTK) and can now protect the frame going back with a Message Integrity Code (MIC).

The second frame is send back from the Supplicant and contains a SNonce making it possible for the Authenticator to resolve a PTK. The Authenticator can now use this PTK to validate the MIC of the second frame aswell.
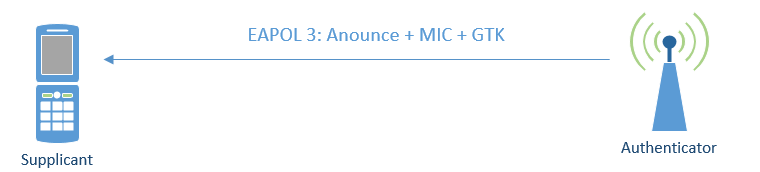
The third frame is send from the Authenticator and now contains Group Temperal Key(GTK) used to encrypt multicast traffic.

The fourth frame is send from the Supplicant to the Autenticator and tells it if the keys were installed or not.
Now is easy to understand why its called “4-way handshake” its because of four messages are exchanged between the Supplicant and the Authenticator. Here is the same exchange thru Wireshark:

Reference:
Certified Wireless Analysis Professional – Study and Reference Guide
Certified Wireless Security Professional – Study and Reference Guide
Youtube link from CWNP and Marcus Burton: https://youtu.be/9M8kVYFhMDw
Leave a comment